Phishing mails asking users to enter their account username and password for “verification” in order to avoid dire consequences is all too common. As anyone who knows the basic anti-phishing procedures will tell you, one of the primary things to look out for is the domain where the verification page takes you to. In all phishing attempts, this is always hosted on an outside site.
But in a recent phishing scam brought to light by security firm Sophos, phishers are attempting to overcome this precaution by using Google Docs to host their phishing forms.
Here's what the message looks like:
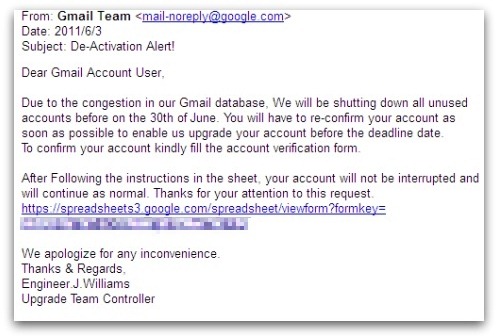
Subject: De-Activation Alert!
Dear Gmail Account User,
Due to the congestion in our Gmail database, We will be shutting down all unused accounts before on the 30th of June. You will have to re-confirm your account as soon as possible to enable us upgrade your account before the deadline date.
To confirm your account kindly fill the account verification form.
After Following the instructions in the sheet, your account will not be interrupted and will continue as normal. Thanks for your attention to this request.
[LINK]We apologize for any inconvenience.
Thanks & Regards,
Engineer.J.Williams
Upgrade Team Controller
If you pay close attention, there are already a few instances that should send your warning bells ringing, such as the improper capitalization of “Following” and grammatical mistake in the phrase “before on the 30th of June”. Even “Upgrade Team Controller” doesn’t sound quite right.
Assuming you missed those signs, there is still the URL to verify whether the email is legitimate. But as the link does point to a webpage hosted somewhere on Google.com, some computer users may believe that the form they are being directed to must be genuine. However, it is actually pointing to a spreadsheet on Google Docs that anybody can create.
By using Google Docs to host their form, phishers are hoping that potential victims will believe it's a genuine Google resource as it is hosted at an authentic Google URL.
As always, users shouldn't forget that no organization, be it Google or your bank, ever asks users to verify their accounts by giving them their passwords. If you receive such email you should ignore it.
[via Search Engine Journal]

Comments
Post a Comment