BlackBox Security Monitor is a kind of spy application software that allows administrators to monitor and oversee user activities on other computers on a network.
The software guides the administrator through a short wizard type program via which the administrator adds computers and users to monitor on BlackBox Security Monitor. It’s possible to monitor activities of only specific users. The program than monitors the following activities and events on the computers:
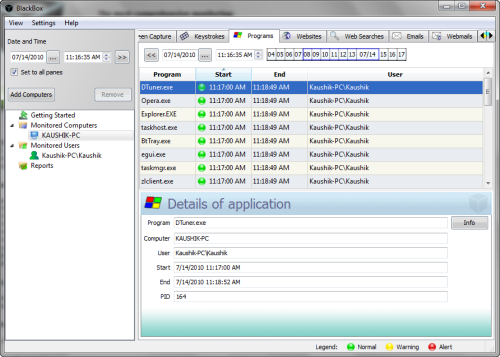
- Every Program launched: when program was started/ended, what is the program name, what is the text in program title
- Every Web site visited: the web site address, when it was, even the IP address
- All Web Searches: what was this search for
- Computer usage time
- All E-Mails sent and received
- All Web Mails sent and received on HotMail/LiveMail, YahooMail, Google GMail, AOL Web Mail
- Instant Messengers chat and conversations via Windows Live Messenger, AOL, Yahoo/ICQ, Jabber, etc
- All keystrokes typed
- Record screen captures in color and high resolution with highest compression rate available
- Total network traffic
If any of these activities triggers an alert, as configured by the administrator for instance, a user exceeds network traffic limit, BlackBox Security Monitor will issue warnings on the administrator’s email or cell phone. The alerts include a summary of events that caused the alert along with a brief usage history.
Several different reports creating options are available from within the program. The administrator, for example, can generate reports for
- 10 Most popular programs
- 10 Most popular Web sites
- 10 Most popular searches on the Web
- 10 Most active Instant Messenger users
- 10 Most active E-Mail users
- etc.
BlackBox Security Monitor offer business enterprises and home networks alike a free solution for robust computer monitoring. It should be noted that the software can also be used to monitor activity on a single computer but the lack of stealth makes it unsuitable to be used as a spying tool. This is not a limitation or flaw because the software is not designed to be used as such.

Comments
Post a Comment