Sometimes, it appears that some software are more prone to vulnerabilities than others. Zero-day exploits and unpatched security holes are all too common with Windows, and applications such as Java and Adobe Flash. While this might be true, the truth is no software is immune from vulnerabilities. Whether the software is in your PC, your phone or in your car, all software has bugs, but who gets attacked and who doesn’t depend on the vendor market share, the motivation of the attackers and the profile of the victim. So how does one keep themselves and their software protected from attackers?
The Enhanced Mitigation Experience Toolkit (EMET) is a free utility from Microsoft that helps prevent vulnerabilities in software from being successfully exploited. EMET achieves this goal by using security mitigation technologies built into Windows, in cases where the developer of the application didn’t opt to do this themselves. By doing so, it enables the end user to beef up the security of a wide variety of third-party software and make them significantly more resistant to exploitation.
EMET can work together with any software, regardless of when it was written or by whom it was written. This includes software that is developed by Microsoft and software that is developed by other vendors. However, you should be aware that some software may not be compatible with EMET.
The Mitigations EMET offers are:
- Structured Exception Handler Overwrite Protection: This mitigation performs Structured Exception Handler (SEH) chain validation and breaks SEH overwrite exploitation techniques.
- Dynamic DEP Data Execution Prevention (DEP): This is a memory protection mitigation that marks portions of a process’ memory non-executable. This makes it more difficult to an attacker to exploit memory corruption vulnerabilities.
- NULL page allocation: This blocks attackers from being able to take advantage of NULL dereferences in user mode. It functions by allocating the first page of memory before the program starts.
- Heap spray allocation: Heap spraying is an attack technique that involves filling a process’ heap with specially crafted content to aid in exploitation. Right now, many attackers rely on their content being placed at a common set of memory addresses. This mitigation is designed to pre-allocate those memory addresses and thus block these common attacks.
- Export Address Table (EAT) Access Filtering: In order to do something useful an exploit generally needs to call functions exposed by Windows. However, in order to call one of these functions, the exploit must first find where it is loaded. This mitigation blocks the most common approach used by exploits to look up the location of a function which involves scanning the export address table of loaded libraries. It is highly effective at blocking exploits currently being used.
- Mandatory Address Space Layout Randomization: ASLR randomizes the addresses where modules are loaded to help prevent an attacker from leveraging data at predictable locations. The problem with this is that all modules have to use a compile time flag to opt into this. Mandatory ASLR forces all modules to be loaded at randomized addresses regardless of what flags they were compiled with. Exploits relying on data at fixed addresses will fail.
- Certificate Trust: SSL Certificate Pinning helps detect Man in the Middle attacks that leverage the Public Key Infrastructure (PKI). EMET comes with specific rules for Microsoft and other popular online services such as Twitter, Facebook, and Yahoo! and enables customers the possibility to create their own customized rules.
How to use Enhanced Mitigation Experience Toolkit
EMET’s protection can be run in three modes – 1) in recommended setting, ASLR and Certificate Trust is forced upon all applications while DEP and SEHOP protection is made applications opt-in. 2) in maximum security mode, all protections are forced upon running applications. 3) in custom mode, users can decide which protection to enforce.
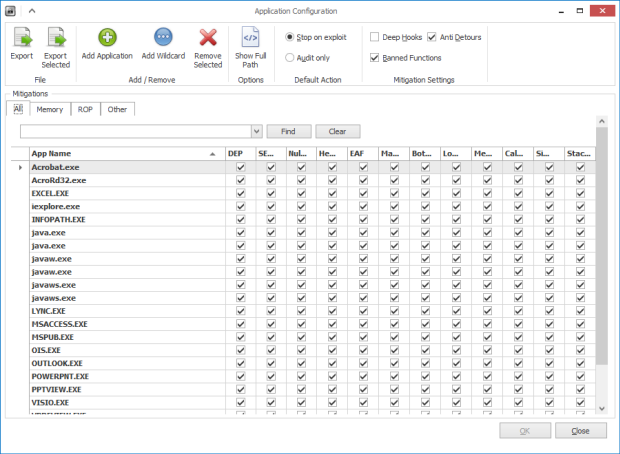
EMET automatically adds protection to Internet Explorer, Microsoft Office, WordPad, Adobe Acrobat and Reader and Java. To add EMET’s protection to another program, follow these steps.
Open EMET, and then click on the “Apps” icon in the toolbar. In the “application configuration” window that opens next, click on the “Add application” button. Using the file picker dialog box, browse to the location of the application executable and select it. All available protections should be automatically applied to the selected application.
Note, that not all applications are compatible with EMET and will crash or refuse to work. Skype and Google Chrome are two examples.


Comments
Post a Comment